01/06/2016
As everyone who is in IT knows, there is a ongoing malware issue which involves malicious Microsoft Word documents that contain virus macros. When these documents are opened via Word, the user's system is silently infected with a virus (normally a variant of CryptoLocker) that encrypts documents, spreadsheets, images etc. and then demands payment for recovery of these images. At that point your only hope is a good backup or owning some Bitcoin (to pay the ransom).
Anti-virus software catches a lot of these, but the viruses in the macros are obfuscated and avoid a significant percentage of detection.
Current "Best Practices" recommend the following:
1. Don't open attachments from unknown senders
2. Disable auto-loading of Macros in Word (and Office in general)
3. Keep anti-virus software up to date
My problem in recommending this to users is that I KNOW for sure that they will still get infected using these "Best Practices" which are not very good at all, and certainly not "Best" which should equal "No infections" but they do not, as any IT person can tell you.
The ability to make these macros avoid detection even by multi-layered virus strategies at the email server and client desktop made us look at new and better ways to prevent them. In the end, after a lot of false starts, we decided to remove the macros from Word documents except for whitelisted senders. Hence the name "Word Macro Killer". We have found this approach to be 100% effective against this email threat.
Here is how we handle macros in Word documents if no virus is found but the document contains a macro:
- Create and attach a harmless PDF or DOCX file that the user can view, to ascertain whether the original file is genuine/harmless. In most cases, they can do their work with the DOCX format and never need to open the original DOC.
- Protect the original document with a password, so that the user cannot easily open it. The password is included in the SpamSentinel Report.txt document that is attached to the document.
- Whitelists can be applied to senders and domains that regularly send documents containing macros.
These Word macro virus documents are currently very effective at evading filters and human detection alike, and, if you check the Bitcoin blockchain, a LOT of money is being paid for ransom to recover encrypted files. We are recommending that everyone with email start stripping the macros from the Word documents to prevent further infections from email messages containing Word macro viruses.
Short lesson in the anatomy of a Word Macro Virus
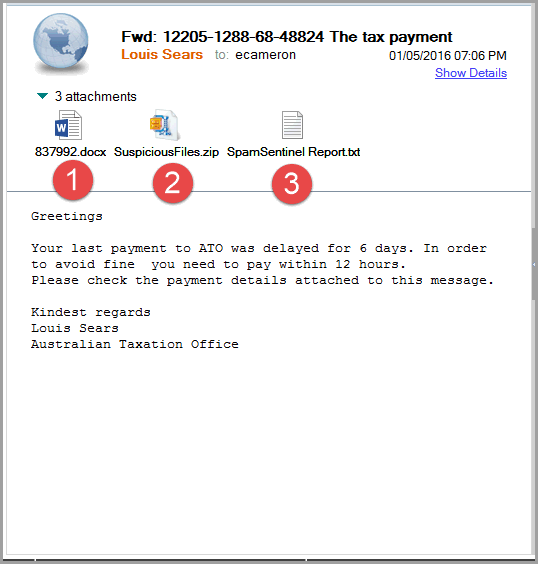
Here is a "typical" email with a Word Macro Virus. These are almost always "generic" as in "Greetings".
1. This is our converted Word document into the harmless DOCX (=cannot contain a macro of any sort).
2. This ZIP file contains the original .DOC with the macro.
3. This file contains the password if you are brave enough (or foolish enough) to open the file.
 Opening the safe DOCX file shows the embedded image that is common in these macros. I have looked at hundreds of these, and they all use the exact same image with the misspelling Macroses. I guess sharing is encouraged in the virus-making community?
Opening the safe DOCX file shows the embedded image that is common in these macros. I have looked at hundreds of these, and they all use the exact same image with the misspelling Macroses. I guess sharing is encouraged in the virus-making community?
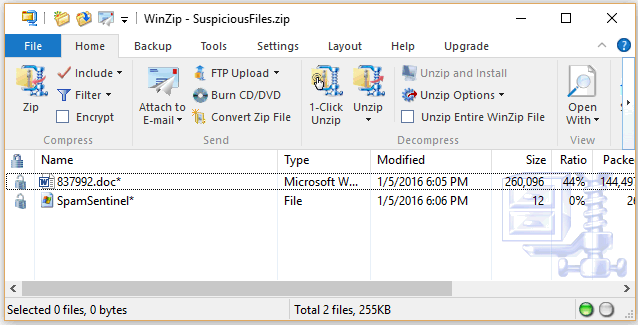
 Here is the password protected ZIP file, requiring you to enter a password before opening the original file.
Here is the password protected ZIP file, requiring you to enter a password before opening the original file.
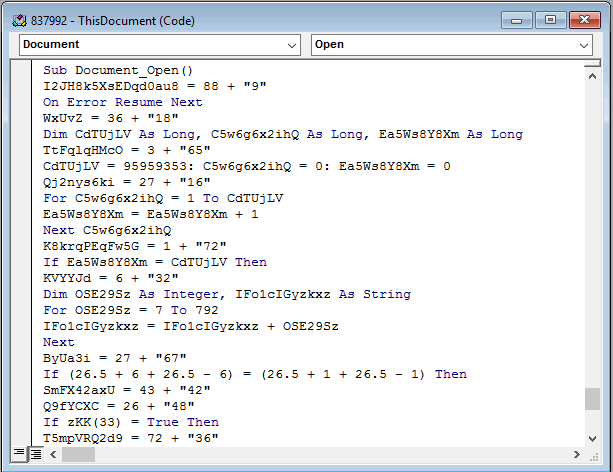
 Here is a sample of the macro code. Notice how it is obfuscated making it unreadable to humans and helping it to avoid detection by anti-virus programs.
Here is a sample of the macro code. Notice how it is obfuscated making it unreadable to humans and helping it to avoid detection by anti-virus programs.
 Blog Tags
Microsoft Macros
Blog Tags
Microsoft Macros